The Shiba Inu community recently faced one of its biggest setbacks after hackers drained millions from Shibarium, the ecosystem’s layer-2 blockchain.
For context, the attack occurred on Sept. 12 and wiped out about $2.4 million in ETH and SHIB, according to an earlier report from The Crypto Basic. Blockchain security platform PeckShield first called the public’s attention to the exploit.
How the Shibarium Hack Occurred
Shortly after the breach, entrepreneur Mario Nawfal revealed how the exploit occurred. Specifically, he explained that the attackers took out a flash loan worth about $1 million in BONE tokens from ShibaSwap.
Afterward, they then delegated those tokens to Shibarium validators, giving them two-thirds majority control. With this control, they signed a malicious state on the network and siphoned 224 ETH and more than 92 billion SHIB from the bridge.

In addition, Nawfal added that the attacker had already compromised ten out of twelve validator keys but still needed the flash-loaned BONE to reach the required majority.
Blockchain data showed that the attacker used part of the stolen funds to repay the flash loan while keeping millions in profit. They also tried to dump around $700,000 worth of KNINE tokens, but every attempt failed after K9 Finance blacklisted their wallet.
As a result, the attackers will not be able to move or use the KNINE assets. Now, the K9 team has introduced a 5 ETH bounty for the attacker to return the KNINE tokens, on-chain data shows.
Meanwhile, in response to the broader exploit, the Shibarium team froze staking and unstaking, moved stake manager funds into a safer multisignature wallet, and brought in security firms Hexens, Seal911, and PeckShield to investigate.
A Merkle Root Exploit
Further, security analysts revealed further information following the exploit. For instance, Tikkala Security noted that several signer keys linked to ShibaSwap had leaked, which led to an even larger loss of about $2.8 million.
It seems like multiple signer keys appear to have leaked in Shibaswap, causing a $2.8M loss today @Shibtoken. The attacker (https://t.co/B9pqiGqIvy) withdrew multiple times by providing legit Merkle leaf exit requests from a root signed by 10 different addresses. The "legit"…
— Tikkala Security (@TikkalaResearch) September 12, 2025
The report explained that the attacker abused Merkle root checkpoints by inserting a seemingly valid root signed by ten addresses. Once the root went live, the attacker could pass off fake exit requests as legitimate and drain more funds across multiple transactions.
Pulse Digital also confirmed this and explained that the Merkle root effectively turned into a skeleton key for ShibaSwap’s rootchain manager contract. The contract treats the root as trustworthy, so once the attacker slipped in a compromised version, they could keep feeding it fabricated proofs and pulling assets out.
Pulse Digital stressed that this kind of weakness shows poor governance and weak key management. They called for ShibaSwap to publish a full timeline of the incident, release the list of signer addresses, and commission an independent audit.
What’s Next: Shiba Inu Ecosystem Team Reacts
Meanwhile, developer Kaal Dhairya also addressed the situation, describing the exploit as a carefully planned attack that may have been in the works for months.
He confirmed that the hacker bought more than 4.6 million BONE through the flash loan, seized validator signing keys, and then drained assets by signing a malicious state.
🚨 Shibarium Bridge Security Update 🚨
Earlier today, a sophisticated ( probably planned for months ) attack was carried out using a flash loan to purchase 4.6M BONE. The attacker gained access to validator signing keys, achieved majority validator power, and signed a malicious…
— Kaal (@kaaldhairya) September 13, 2025
Dhairya noted that the stolen BONE delegated to Validator 1 remained locked due to delays surrounding unstaking efforts. This accorded the team the opportunity to freeze those funds. According to him, the team immediately paused staking features and moved stake manager funds into a hardware wallet protected by a six-out-of-nine multisignature setup.
The developer noted that they were still working to determine whether the breach came from a server compromise or a developer machine. According to Dhairya, authorities have joined the investigation, though the team remains open to negotiating with the hacker if they return the stolen funds.
Shiba Inu ecosystem marketer Lucie described the exploit as an example of social engineering, something that has struck many crypto projects before. She stressed that the developers are working around the clock with security experts and law enforcement to secure the network.
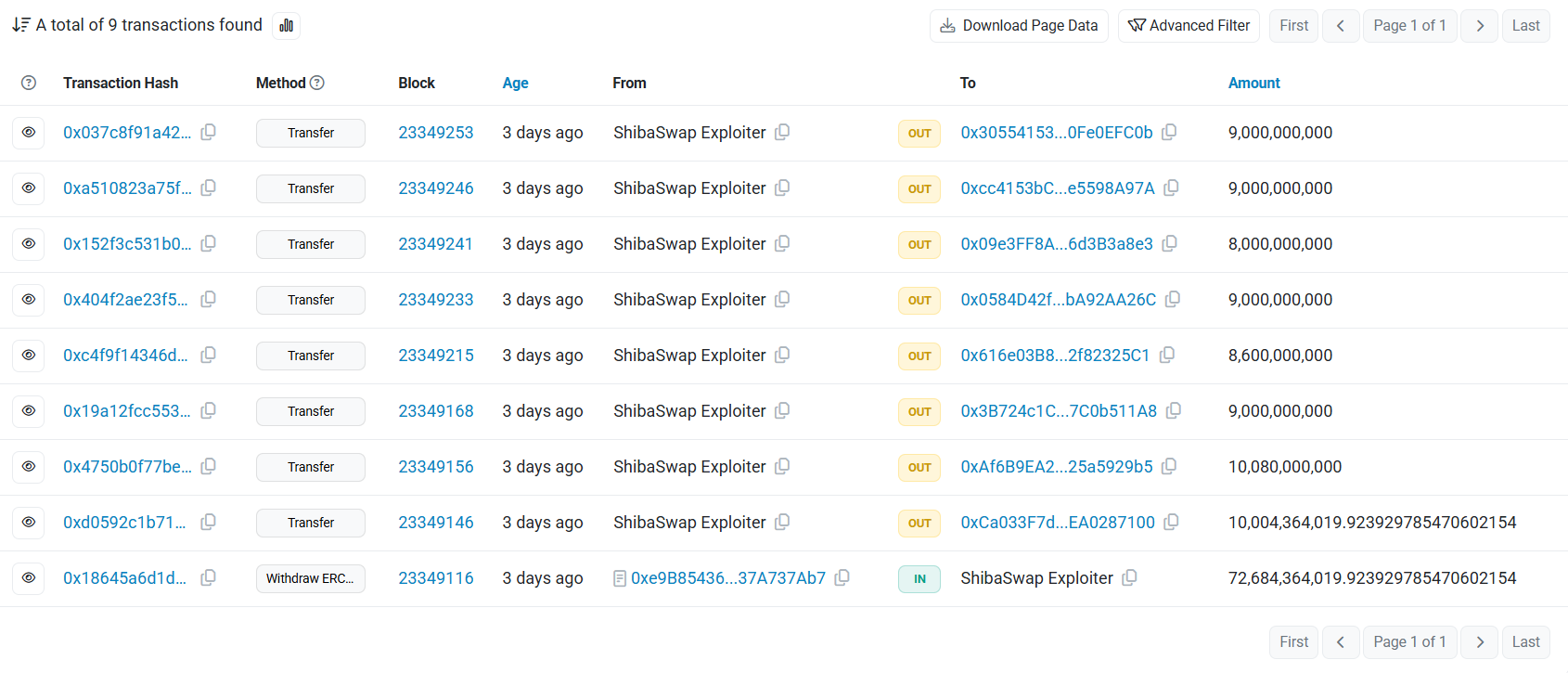
Following the exploit, the hackers moved the Shiba Inu tokens to a central address and then routed them to multiple wallets. At press time, these wallets still hold the tokens, with the balance on each of them ranging from 8 billion to 10 billion SHIB.
DisClamier: This content is informational and should not be considered financial advice. The views expressed in this article may include the author's personal opinions and do not reflect The Crypto Basic opinion. Readers are encouraged to do thorough research before making any investment decisions. The Crypto Basic is not responsible for any financial losses.



